The true security of intelligently interconnected IoT edge nodes
The Internet of Things (IOT) has set off one of the biggest technology waves in recent decades. It is expected that by 2015, 50 billion devices will be interconnected to form a network that may cover everything around us. The Internet of Things will span industrial, commercial, medical, automotive and other applications, affecting billions of people. Given its wide range of influences on individuals, institutions and systems, security has become the most critical component of any IoT system, and the concept that any responsible commercial IoT company must truly grasp security is widely recognized.
When evaluating the vulnerability of the IoT network, developers focused on the most basic element—the edge node. As a "thing" in the Internet of Things, a large number of sensors and actuators provide data to the Internet of Things and execute instructions from the cloud or users interacting with computers, mobile phones, in-vehicle systems, smart appliances or other platforms. Edge nodes are usually small, low-cost smart devices, but because of the limited resources they access, they are often mistakenly considered vulnerable. The servers that interact with the edge nodes and the networks connected to them already have mature security technologies, and edge nodes have not yet had such technologies.
When it comes to protecting such systems, people often regard "encryption" and "security" as equal, but in fact it is only one aspect of the security problem. One of the first tasks in creating a secure environment is to securely discover and prove the identity of the devices connected to your network. You must first determine who is connecting to the network, because if secure authentication is not established in advance, encryption and transport layer security protocols (such as SSL/TLS) do "protect" those visitors who should not enter your network at all.
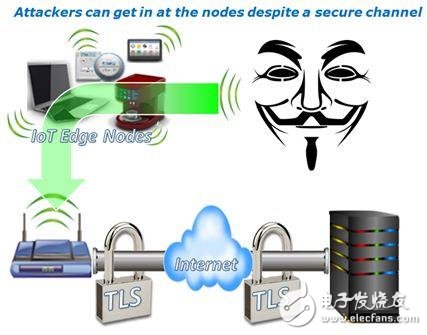
Figure 1. In spite of the secure channel, an attacker can still invade the network from an edge node.
In order to better understand the security of the node, let us use the online banking account to make an analogy. Start by creating a secure (ie encrypted and authenticated) connection between your computer and the bank's website (this is an https link). However, this secure link only verifies your computer when creating an encrypted communication channel between your computer and the bank, and does not authenticate you. At this point, the bank still doesn't know if you are a liar. You will need to enter your password. This password is your encryption key, so in theory, only you and the bank know. Once it is sent to the bank it will be compared to your saved password. If it matches, then for the bank, this proves that you are the person you claim to be. As can be seen from this example, the security of online banking is provided by two levels: 1) the transport layer establishes a secure connection, and 2) the application layer authenticates (certifies) your identity. Similarly, if the Internet of Things is given enough attention, the node security of the Internet of Things must also be provided by multiple layers.
IoT nodes also use Transport Layer Security protocols to create secure connections to the cloud. But to achieve true security, IoT nodes must also gain application layer security. This means that not only the communication channel (ie, the pipe), but the node itself also needs to be authenticated. In addition to channel authentication, the application layer should establish encryption and data integrity checking mechanisms to protect data flowing through the pipeline.
With this in mind, these IoT devices are often simple and small devices with little or no interaction, so they also introduce a new network connectivity paradigm. This usually leads to a variety of questions. On the one hand, concerns about infrastructure security have raised questions about “how to determine that an IoT device is trustworthy? Even how to know that a real IoT device is connected to your network, rather than pretending to be an IoT node. A malicious intrusion device?". This has been countered by some real problems. For example, "Someone knows that my thermostat is set a few degrees and what is the big deal?", "Who cares if anyone knows if my lights are on?", "Who?" Want to know if my pedometer records me a few steps?".
If you not only consider which data the device has accessed, but also start to care about which data the device has accessed over the network, it will encounter more substantial problems. Several widely reported data leakage incidents are caused by non-secure network nodes through fake identity, and malicious intruders can pretend to be an IoT node to enter the corporate network. Once on the network, security becomes more vulnerable, and they eventually have access to the victim's customer database and disrupt the production process. If a malicious intruder can access and control the operation of the node itself in addition to accessing the cloud service, then determining the identity (authentication) of the node will be an extremely important consideration.
Although existing network security technologies such as SSL/TLS can well protect the communication channels between the invading edge nodes and servers, they are not invincible - they cannot prevent non-intrusive attacks. It's easy to see that if an attacker controls an edge node, SSL/TLS will not help.
Strict security consists of three basic elements, the acronym is "CIA":
â— Confidentiality - ConfidenTIality: Data stored or being sent should be visible only to the authorized person;
â— Integrity - Integrity: Messages sent should not be modified before reaching the destination;
â— Authenticity - AuthenTIcity: It can be assured that "the sender of the message is the claimed person."
There are many techniques for meeting the requirements of these elements, and the commonality is the use of a key or private key as a unique part of the verification identification tag. How to manage the storage and communication of these keys determines the security of the system.
The challenge now is to achieve edge node security while ensuring that available computing power, memory, power, and budget are maintained to a limited extent. The purpose of this paper is to identify key security policies for edge nodes, to illustrate the central role that keys play in all security solutions, and to outline successful key management techniques.
Cascading benefits of secure identity
Once a node or device is identified as "trusted," you can get countless other benefits. Includes secure communications, ecosystem controls, and secure storage.
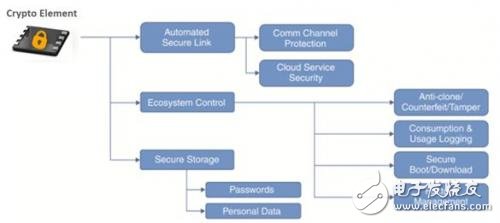
Figure 2. The many benefits that an authenticated node can get.
As you can see, once you can verify that the IoT device matches your claim, you get the benefits you can only have in a trusted, secure environment.
Recorder speaker is a kind of micro speaker unit which uses a diaphragm made of Mylar material. Mylar speakers are of ultrathin design and lightweight and clear voice. It is widely used in education industry (storyteller, voice E-book, repeater, reading pen-).
There are two types of Mylar speakers from the shapes:
1) Round shapes, we have products from 10mm to 57mm in diameter.
2) Oblong shape, we have products in sizes of 1510/1712/1813-..

FAQ
Q1. What is the MOQ?
XDEC: 2000pcs for one model.
Q2. What is the delivery lead time?
XDEC: 15 days for normal orders, 10 days for urgent orders.
Q3. What are the payment methods?
XDEC: T/T, PayPal, Western Union, Money Gram.
Q4. Can you offer samples for testing?
XDEC: Yes, we offer free samples.
Q5. How soon can you send samples?
XDEC: We can send samples in 3-5 days.
Recorder Speaker
Recorder Speaker,Car Recorder Speaker,Recording Pen Speaker,Dvr Speaker
Shenzhen Xuanda Electronics Co., Ltd. , https://www.xdecspeaker.com